Malicious Attacks Cause of Most Data Breaches
Malicious or criminal attacks accounted for the main source of data breaches during the first year of operation of Australia’s Notifiable Data Breaches Scheme, according to a 12‑month Insights Report release this week by the by the Office of the Australian Information Commissioner (OAIC).
However, this figure turns around in the health sector, where human error was the leading cause of data breaches (55%), compared with an average of 35% for all sectors
There were 964 data breach notifications under the NDB scheme from 1 April 2018 to 31 March 2019 an increase of 712% over the previous 12 months when reporting was voluntary.
The vast majority of breaches (83%) affected less than 1000 people.
Malicious or criminal attacks accounting for 60 per cent of data breaches, or 580 notifications reported to the OAIC in the period. Of these, 394 data breaches (68 per cent) are attributed to incidents resulting from common cyber threats such as phishing, malware, ransomware, brute‑force attacks, compromised or stolen credentials and other forms of hacking.
The remaining 186 data breaches (32 per cent) attributed to a malicious or criminal attack were the result of theft of paperwork or a data storage device, social engineering or impersonation, or an act of a rogue employee or insider threat.
Finance and health were the top industry sectors to report data breaches. The report notes this is likely a reflection of the high‑volume data holdings in these industries and may also indicate comparatively mature processes for identifying and reporting data breaches. Both sectors face strong regulatory scrutiny around data protection, and the costs associated with data breaches may also be higher.
Notably, phishing and spear phishing continue to be the most common and highly effective methods by which entities are being compromised - whether large or small - in Australia or internationally. Within the period, a total of 153 data breaches were attributed to this method.
Attackers typically use phishing to elicit credentials - usually a username and password - from a user to gain access to systems. Attacker techniques continue to evolve in this area, making phishing emails increasingly difficult to detect without sustained and focused user education.
After phishing, the second most prevalent cyber incident data breach involved compromised or stolen credentials where the method of compromise was not known by entities reporting to the OAIC. An explanation may be the growing prevalence of ‘credential stuffing’ attacks using breached user credentials that have been leaked or posted online.
Excluding cyber breaches, social engineering or impersonation and actions taken by a rogue employee or an insider threat were also significant contributors to data breaches, as was theft of paperwork or data storage devices.
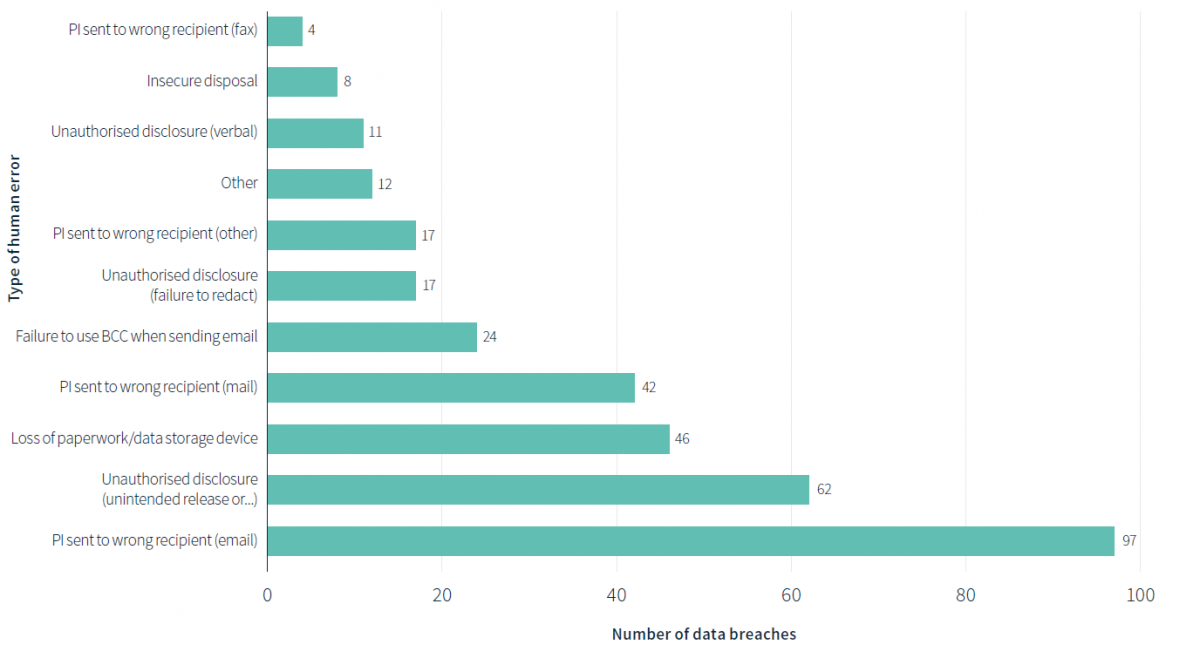
Human error breaches - all sectors, from 1 April 2018 to 31 March 2019
The full report is available HERE
