Signals Directorate releases 2023 Cyber Threat Report
The Australian Signals Directorate has released its fourth ASD Cyber Threat Report, which found almost half of reported incidents came from Federal, State or Local Government. Malicious cyber activity continued to increase in frequency, cost and severity compared to the previous year.
The top 3 cybercrime types for business were: email compromise; business email compromise (BEC) fraud; and online banking fraud.
The cost of cybercrime to businesses increased by 14% compared to the previous financial year. Small businesses experienced an average financial loss of $A46,000, while cybercrimes cost medium businesses an average of $A97,200, and large businesses an average of $A71,600.
“Cybercrime is a multibillion-dollar industry that threatens the wellbeing and security of every Australian. Cybercrime covers a range of illegal activities such as data theft or manipulation, extortion, and disruption or destruction of computer-dependant services. In 2022–23, cybercrime impacted millions of Australians, including individuals, businesses and governments. These crimes have caused harm and continue to impose significant costs on all Australians,” the report notes.
During the 2022-23 financial year, there were nearly 94,000 reports of cybercrime submitted to ReportCyber, an increase of 23% compared to the previous financial year. On average, that’s one report received every 6 minutes.
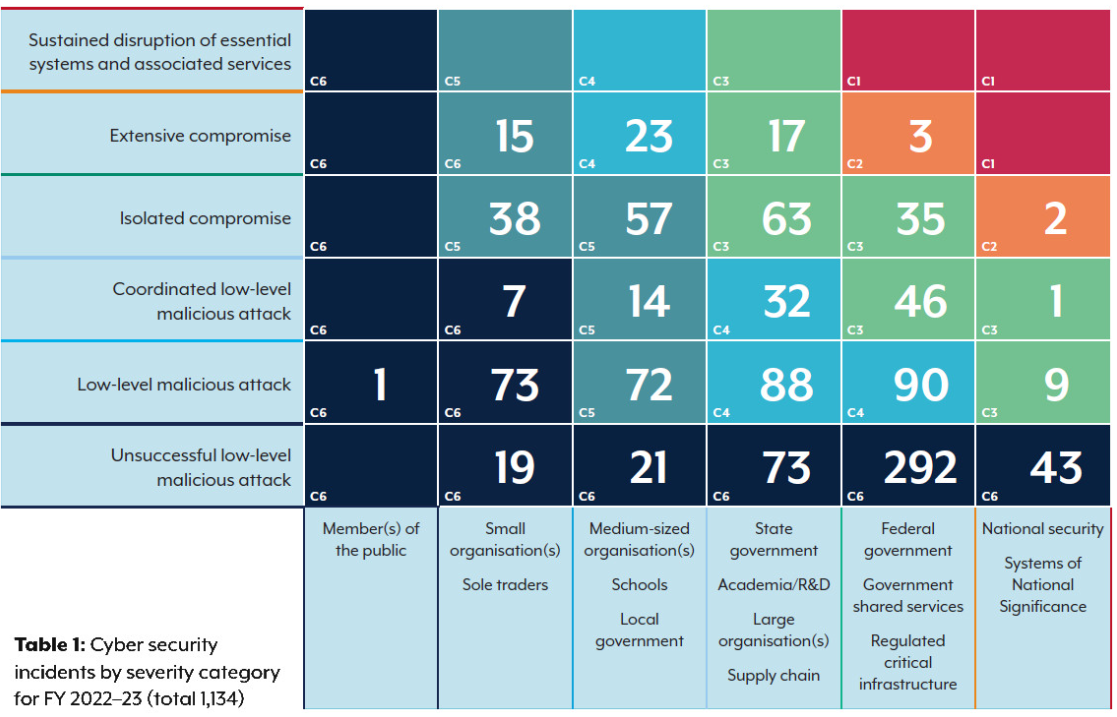
ASD responded to over 1,100 cyber security incidents from Australian entities. There were 143 related to critical infrastructure, an increase by almost one-third in the 22-23 financial year.
About 57% of cyber incidents reported by critical infrastructure entities involved compromised accounts or credentials; compromised assets, networks or infrastructure; and denial of service attacks.
“In 2022–23, ASD joined international partners to call out Russia’s Federal Security Service’s use of ‘Snake’ malware for cyber espionage, and also highlighted activity associated with a People’s Republic of China state-sponsored cyber actor that used ‘living-off-the-land’ techniques to compromise critical infrastructure organisations.
Case study: A network compromise at the Shire of Serpentine Jarrahdale
The rural Shire of Serpentine Jarrahdale, 45 kilometres from the Perth CBD, may seem an unlikely place for malicious cyber activity to unfold. But, in early 2023, the Shire experienced a network compromise.
Shire ICT Manager Matthew Younger said the malicious cyber actor took advantage of a public-facing system. ‘We’re quite diligent with our patching, but unfortunately we missed an update to our remote work server,’ Mr Younger said.
Before taking immediate remediation action, the Shire’s ICT team held a conference call with ASD to discuss the best way to manage the compromise, and Mr Younger said ASD’s help was first-class. ‘We put a perimeter around the compromised server, checked for lateral movement, and gathered evidence to work out what happened. Everything we found led back to the importance of the Essential Eight.’
ASD also sent an incident responder to help the Shire’s ICT team capture virtual machine snapshots and log data. ASD handles incident data with strict confidentiality, and such data helps its analysts understand how cyber security incidents occur and produces intelligence to help build the national cyber threat picture and to prevent further attacks.
Mr Younger said that after the compromise, the Shire doubled-down on its efforts to implement ASD’s Essential Eight. ‘We enforced passphrases, we improved our information security policies, and we improved our user security training. We also validated our controls through penetration testing and phishing exercises.’
Mr Younger credits much of the Shire’s success to its agile leadership who, with limited resources, foster the right security culture to both respond to cyber threats and implement mitigations.
The full report is available HERE
