Does DIY ediscovery measure up?

David McGrath explores the challenges of insourcing ediscovery. When does it make sense to leave it to the experts and what are the tools, processes and resources you need to be aware of?
A thriving and nuanced ediscovery industry exists in Australia, with many of our providers having been around for some time and quite rightly entitled to consider themselves world class.
There is in fact a growing trend towards insourcing some aspects of ediscovery. The 2009 Litigation Trends Survey by international law firm Fulbright & Jaworski LLP found that around one half of their respondents insourced an aspect of ediscovery.
We all know ediscovery can be expensive so wouldn’t it make sense to do at least some of it yourself? You might be able to save some money whilst creating and retaining valuable knowledge about your processes and data assets for later reuse. Moreover, it can be an important driver for an improved information management strategy.
Obviously, the largest driver for insourcing ediscovery functions is your litigation profile. You can think of your litigation profile in terms of how often you anticipate being involved in litigation, or regulatory investigations, and what risk that poses to the organisation.
Some industries such as construction, pharmaceutical, financial services tend to have higher litigation profiles than others. A good initial test of course is the size of your current litigation spend.
What Aspects to Insource?
So what does it mean to insource ediscovery and which parts of it are candidates for it?
To answer this question, lets begin with the EDRM framework (www.edrm.net) developed by George Socha and Tom Gelbmann (pictured below) and focus on the left hand side.
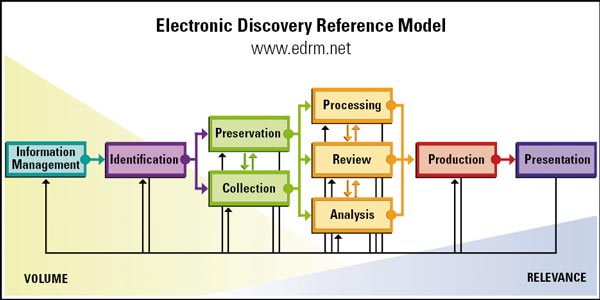
The steps that offer the greatest potential for insourcing are information management, identification, preservation and collection. The reasons for this are many:
Its your data! Subject to any outsourcing, cloud computing and Web 2.0 social technology considerations (flinging your data to unknown corners of the planet), it is assumed that the great majority of the data which needs to be considered for ediscovery is in your possession and under your control. Once the right volume of data has been identified, preserved and collected, a working copy can be easily passed onto your external lawyers and their bureaus for processing and review. Whether or not you use external service providers to assist, you need to be heavily engaged in these early stages of ediscovery anyway.
Technical and business knowledge. Again, irrespective of who else is involved in the ediscovery effort, knowledge of the business, how information is captured, stored and disposed of, how the technology is set up and used will be key to these initial discovery steps.
Compliance risk mitigation. The greatest potential for ediscovery risk occurs early in the process. A failure to diligently scope the initial identification of potentially relevant data or failure to preserve potentially relevant data when litigation is anticipated can lead to disastrous outcomes. In America, the courts are becoming increasing intolerant of ediscovery mistakes, with increasing and more frequent sanctions imposed whenever evidence is ‘spoliated’ i.e. damaged or destroyed. With the Australian courts coming under increasing pressure to reduce the costs of justice, it is only a matter of time before that same intolerance is shared by our own courts.
Cost management. In e-discovery, the biggest driver of costs is data volume. Whilst ensuring that you not miss relevant data in your discovery, it is equally important from a cost perspective that you “trim the fat” from your data set early. Better still don’t collect too much of it in the first place. A good collection methodology together with effective data filtering systems will assist in keeping the data which needs to be processed and reviewed as trim as possible. It is important to note that, generally speaking, each successive step in the ediscovery process incurs a greater per document cost, so getting rid of unnecessary data is a crucial aspect of efficient management.
Iterative Process. What is emerging now is an understanding that to get the balance right between compliance and cost management, an iterative process is beneficial. This may be as simple as running different keyword searches and then sampling the results to see how effective those searches were at collecting the right data. The search terms can then be adjusted.
Information management. There is some debate over whether this is a formal part of the ediscovery process. What is clear is the impact that information management has on the success of your ediscovery effort. Information which is clearly categorised, organised and managed will be much easier to scope, collect and preserve than unstructured, scattered and disparate data. Depending on your litigation risk profile, those additional costs and risks can be another powerful argument for spending more earlier in the information lifecycle on information management.
The steps to the right of the EDRM diagram, such as processing, analysis, review and production, are more specialised ediscovery and legal activities. As an example, the processing of electronic data in preparation for upload into a review tool is not for the faint-hearted and should not be attempted by anyone without specialist experience. There are also strong grounds to always outsource investigations involving computer forensics, not just from a competency perspective but to ensure that the investigation remains at arms length from the organisation.
Getting Started
A lot can be achieved by simply becoming more aware of the ediscovery process, and obligations, and then ensuring that the organisation has a plan for when litigation occurs.
Implementing some simple measures designed to avoid destruction of evidence once litigation is anticipated may well prevent a costly sanction and provide the biggest return on investment for your ediscovery insourcing effort. This step is important enough in the United States to have it its own name – “litigation hold”. The aim here is not so much to achieve best practice as a reasonable practice. It should examine areas such as backup tape rotation cycles, suspending document destruction operations and advising employees not to destroy potentially relevant documents.
Your ediscovery plan can go further and define processes for the identification and collection of data. Having a consistent approach built around properly considered policies and processes will assist. If something does goes wrong it’s nice to be able to say “look at our process and see what we have done right”.
It is important to note that putting procedures and policies in place particularly for the ‘litigation hold’ phase does not have to include the acquisition of any technology. It may be that your policy is to engage external partners to assist you with any work required at this stage.
Adding Technology
There is a whole spectrum of technologies to support the functions of preservation through to search, collection and early case assessment.
The technologies are available on a component basis as well as ‘cradle to grave’. How you mix and match these technologies depends upon your skill profile and how much you want to bite off. If you are adding technology, it is important to note that you will need skilled staff to drive it.
It is also important to match the technologies with your data profile and ediscovery practices. For example, a full text search tool may be able to search unstructured data but how will it connect to SharePoint, email archives, database files, document or content management systems.
Also, once you identify potentially relevant hits how do you ensure that they are preserved, collected and dealt with in a forensically sound way. There are a range of questions that need to be answered here before the technology can be considered fit for the task.
There are a number of technologies branding themselves as either early case assessment or information management tools (or both). They are sometimes available as licensed software or more typically, an appliance solution. They offer functionality across the spectrum of search, collection, preservation, analysis and review. They are not forensic tools although they will usually offer forensically sound collection.
In effect, they offer organisations the opportunity to quickly search their electronic data and review it, on an iterative basis if necessary, so that they can quickly get a feel for their case and have a strong platform for further ediscovery, if required.
With the costs of ediscovery sometimes becoming disproportional to what’s at stake in the case, understanding exactly what your documentary evidence says early in the case may well prove a crucial factor in deciding whether to fight the case or settle gracefully.
Insourcing ediscovery does not mean you have to do all of it by yourself. There are a variety of partners from consultants to full service providers to law firms who can assist you to design policies and procedures for dealing with ediscovery through to providing assistance with your ediscovery effort.
Whether you choose to call it insourcing ediscovery or better information management, there is great scope for taking more control of ediscovery.
David McGrath is a Sydney-based solicitor and experienced ediscovery expert.The next article in this article in this series, to be published in the September-October 2010 edition of Image & Data Manager magazine, we will look in more detail at the specifics of ediscovery insourcing including process, data management and a brief review of the software providers.
